Basics
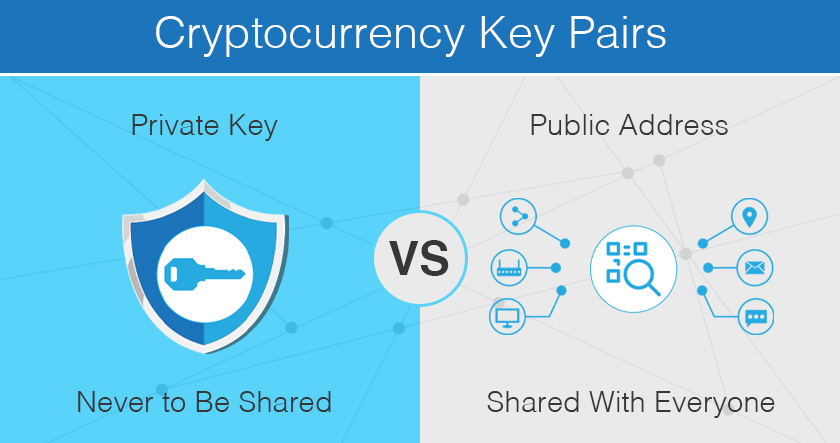
- By using cryptography, you can create a key pair consisting of a public key and a private key.
- The public key is used to receive funds, similar to your bank account number. It can be publicly shared without risking losing your funds.
- The private key is used to spend the funds, similar to your bank account password. You should never disclose it.
- A wallet helps you to generate and manage such kind of key pairs because they are long alphanumeric strings and not easy to memorize.
- To make bitcoin transaction easier in daily life, the public key is converted to a much shorter bitcoin address (33 or 34 characters) through a series of mathematical functions.
- On most occasions, we use “public key” and “address” interchangeably.
- We present our bitcoin address instead of the public key when we want to receive funds. We rarely see our actual public keys in bitcoin daily usage.
- You can also think of your phone number as your bitcoin address, and it allows others to call you easily. Your SIM card is your private key and if you lose it, you lose control of your identity. The IMEI identifier of your phone is similar to the public key, which can be used to uniquely identify you, but it is too long and used internally and rarely shown to users.
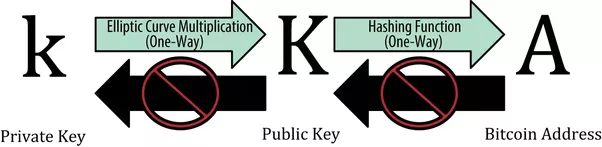
- From your private key, we can calculate your public key; and thru your public key, we can calculate your bitcoin address. But it cannot be done in the opposite direction. Therefore, as long as you keep your private key in a safe place, you are in full control of your fund.
Intermediate
- In Bitcoin, we use elliptic curve multiplication as the basis for its cryptography. The curve determines the mathematical relationship between the public key and the private key.
- The private key is not used to encrypt your fund, instead, to sign a message, usually a transaction. It is similar to your signature on the cheque, which enables you to prove your ownership and spend the fund in the bank.
- By applying a signing algorithm (e.g. DSA) between your private key and the transaction message, a unique digital signature can be generated. Anyone with your public key can verify the signature was generated by you and the message was not altered in transit.
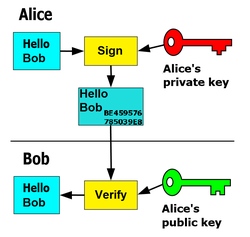
- This useful property allows the private key owner to prove its ownership of the source of the information without revealing the private key, and anyone with the public key to verify the signature without knowing the private key.
- The relationship between the private key and public key is fixed, but can only be calculated in one direction, from private to public. We call such kind of relationship as “asymmetric”. It is guaranteed by math.
- Such kind of asymmetric cryptography has been widely used on the internet nowadays to prove the authenticity of a digital identity, such as a website, an email message, a electronic document, a bank transaction and so on.
Advanced
- ECDSA or Elliptic Curve Digital Signature Algorithm is the core of bitcoin cryptographic algorithm which defines how bitcoin private key and public key are generated.
- From the public key, we can derive the “raw” bitcoin address using SHA256 and RIPEMD160 one-way functions.
- To help human readability, avoid ambiguity and protect against errors, we use “Base58Check” to encode the “raw” bitcoin address, which is the ultimate address (33 or 34 characters) we see in daily transactions.
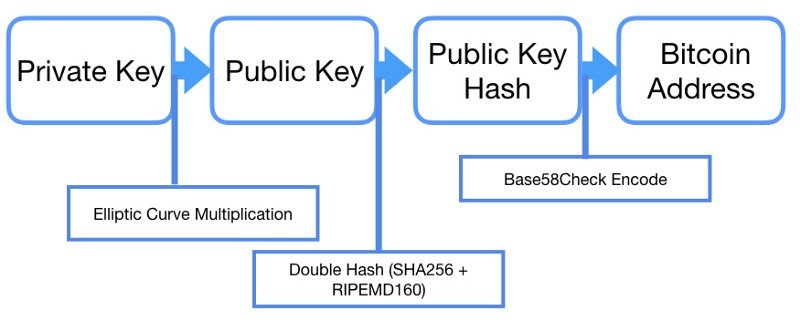
- Base58 uses all letters (lowercase & uppercase) and numbers except (0, O, l, I) to represent the 160-bit “raw” bitcoin address.
- Base58Check adds version number and error-checking code at the beginning and end of the address, which boosts its flexibility and security.